publications
most recent publications
2023
- Tech Report
 Capability Hardware Enhanced RISC Instructions: CHERI Instruction-Set Architecture (Version 9)Robert N. M. Watson , Peter G. Neumann , Michael Roe , and 23 more authorsSep 2023Version 9
Capability Hardware Enhanced RISC Instructions: CHERI Instruction-Set Architecture (Version 9)Robert N. M. Watson , Peter G. Neumann , Michael Roe , and 23 more authorsSep 2023Version 9This technical report describes CHERI ISAv9, the ninth version of the CHERI architecture being developed by SRI International and the University of Cambridge. This design captures thirteen years of research, development, experimentation, refinement, formal analysis, and validation through hardware and software implementation.
CHERI introduces an architecture-neutral capability-based protection model, which has been instantiated in various commodity base architectures to give CHERI-RISC-V, Arm’s prototype Morello architecture, and (sketched) CHERI-x86-64. It enables software to efficiently implement fine-grained memory protection and scalable software compartmentalization, by providing strong, deterministic, efficient mechanisms to support the principles of least privilege and intentional use in the execution of software at multiple levels of abstraction, preventing and mitigating vulnerabilities. Design goals include incremental adoptability from current ISAs and software stacks, low performance overhead for memory protection, significant performance improvements for software compartmentalization, formal grounding, and programmer-friendly underpinnings.
CHERI blends traditional paged virtual memory with an in-address-space capability model that includes capability values in registers, capability instructions, and tagged memory to enforce capability integrity. This hybrid approach addresses the performance and robustness issues that arise when trying to express more secure, privilege minimising programming models, above conventional architectures that provide only MMU-based protection. CHERI builds on the C-language fat-pointer literature: its capabilities can describe fine-grained regions of memory, and can be substituted for data or code pointers in generated code, protecting data and improving control-flow robustness. Strong capability integrity and monotonicity properties allow CHERI to express a variety of protection idioms, from enforcing valid C-language pointer provenance and bounds checking to implementing the isolation and controlled communication structures required for software compartmentalization.
CHERI’s hybrid approach allows incremental adoption of capability-oriented design: critical components can be ported and recompiled to use capabilities throughout, providing finegrain memory protection, or be largely unmodified but encapsulated in ways that permit only controlled interaction. Potential early deployment scenarios include low-level software Trusted Computing Bases (TCBs) such as separation kernels, hypervisors, and operating-system kernels, userspace TCBs such as language runtimes and web browsers, and particularly high-risk software libraries such as data compression, protocol parsing, and image processing (which are concentrations of both complex and historically vulnerability-prone code exposed to untrustworthy data sources).
CHERI ISAv9 is a substantial enhancement to prior ISA versions. CHERI-RISC-V has replaced CHERI-MIPS as the primary reference platform, and CHERI-MIPS has been removed from the specification. CHERI architectures now always use merged register files where existing general-purpose registers are extended to support capabilities. CHERI architectures have adopted two design decisions from Arm Morello: 1) CHERI architectures now clear tags rather than raising exceptions if an instruction attempts a non-monotonic modification of a capability; and 2) DDC and PCC no longer relocate legacy memory accesses by default. CHERI-RISC-V has received numerous updates to serve as a better baseline for an upstream standard proposal including a more mature definition of compressed instructions in capability mode. CHERI-x86- 64 now includes details of extensions to existing x86 instructions and proposed new instructions in a separate ISA reference chapter along with various other updates.@techreport{2023cheri_architecture, author = {Watson, Robert N. M. and Neumann, Peter G. and Roe, Michael and Almatary, Hesham and Anderson, Jonathan and Baldwin, John and Barnes, Graeme and Chisnall, David and Clarke, Jessica and Davis, Brooks and Eisen, Lee and Wesley Filardo, Nathaniel and Fuchs, Franz A. and Grisenthwaite, Richard and Joannou, Alexandre and Laurie, Ben and Markettos, A. Theodore and Moore, Simon W. and Murdoch, Steven J. and Nienhuis, Kyndylan and Norton, Robert and Richardson, Alexander and Rugg, Peter and Sewell, Peter and Son, Stacey and Xia, Hongyan}, title = {Capability Hardware Enhanced RISC Instructions: CHERI Instruction-Set Architecture (Version 9)}, institution = {University of Cambridge}, year = {2023}, type = {}, number = {987}, address = {15 JJ Thomson Avenue, Cambridge CB3 0FD, United Kingdom phone +44 1223 763500 }, month = sep, note = {Version 9}, publisher = {Cambridge}, annote = {} }
2020
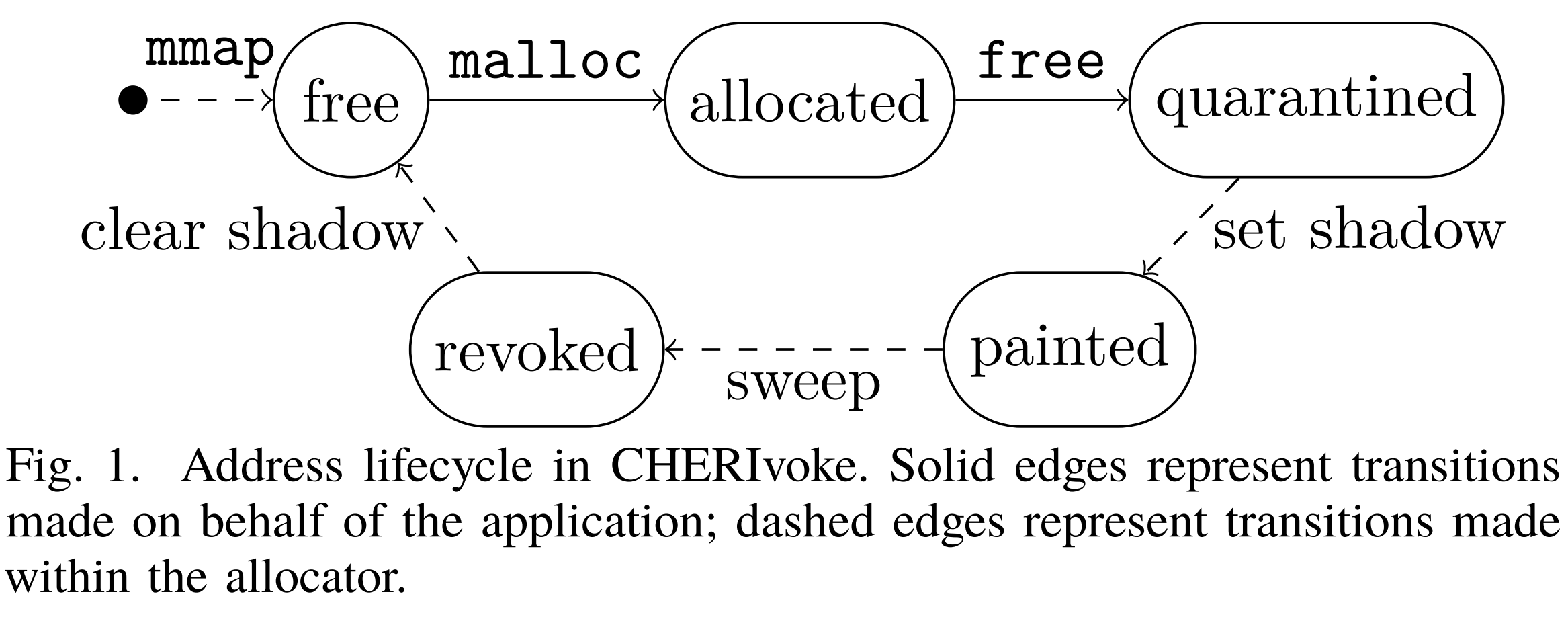
- Cornucopia: Temporal Safety for CHERI HeapsNathaniel Wesley Filardo , Brett F. Gutstein , Jonathan Woodruff , and 21 more authorsIn 2020 IEEE Symposium on Security and Privacy (SP) , Sep 2020
Use-after-free violations of temporal memory safety continue to plague software systems, underpinning many highimpact exploits. The CHERI capability system shows great promise in achieving C and C++ language spatial memory safety, preventing out-of-bounds accesses. Enforcing language-level temporal safety on CHERI requires capability revocation, traditionally achieved either via table lookups (avoided for performance in the CHERI design) or by identifying capabilities in memory to revoke them (similar to a garbage-collector sweep). CHERIvoke, a prior feasibility study, suggested that CHERI’s tagged capabilities could make this latter strategy viable, but modeled only architectural limits and did not consider the full implementation or evaluation of the approach.
Cornucopia is a lightweight capability revocation system for CHERI that implements non-probabilistic C/C++ temporal memory safety for standard heap allocations. It extends the CheriBSD virtual-memory subsystem to track capability flow through memory and provides a concurrent kernel-resident revocation service that is amenable to multi-processor and hardware acceleration. We demonstrate an average overhead of less than 2% and a worstcase of 8.9% for concurrent revocation on compatible SPEC CPU2006 benchmarks on a multi-core CHERI CPU on FPGA, and we validate Cornucopia against the Juliet test suite’s corpus of temporally unsafe programs. We test its compatibility with a large corpus of C programs by using a revoking allocator as the system allocator while booting multi-user CheriBSD. Cornucopia is a viable strategy for always-on temporal heap memory safety, suitable for production environments.@inproceedings{2020cornucopia, author = {Wesley Filardo, Nathaniel and Gutstein, Brett F. and Woodruff, Jonathan and Ainsworth, Sam and Paul-Trifu, Lucian and Davis, Brooks and Xia, Hongyan and Tomasz Napierala, Edward and Richardson, Alexander and Baldwin, John and Chisnall, David and Clarke, Jessica and Gudka, Khilan and Joannou, Alexandre and Theodore Markettos, A. and Mazzinghi, Alfredo and Norton, Robert M. and Roe, Michael and Sewell, Peter and Son, Stacey and Jones, Timothy M. and Moore, Simon W. and Neumann, Peter G. and Watson, Robert N. M.}, booktitle = {2020 IEEE Symposium on Security and Privacy (SP)}, title = {Cornucopia: Temporal Safety for CHERI Heaps}, year = {2020}, volume = {}, number = {}, pages = {608-625}, keywords = {Integrated circuits;RNA;Security;Privacy;Licenses}, dimensions = {true}, doi = {10.1109/SP40000.2020.00098} }
2019
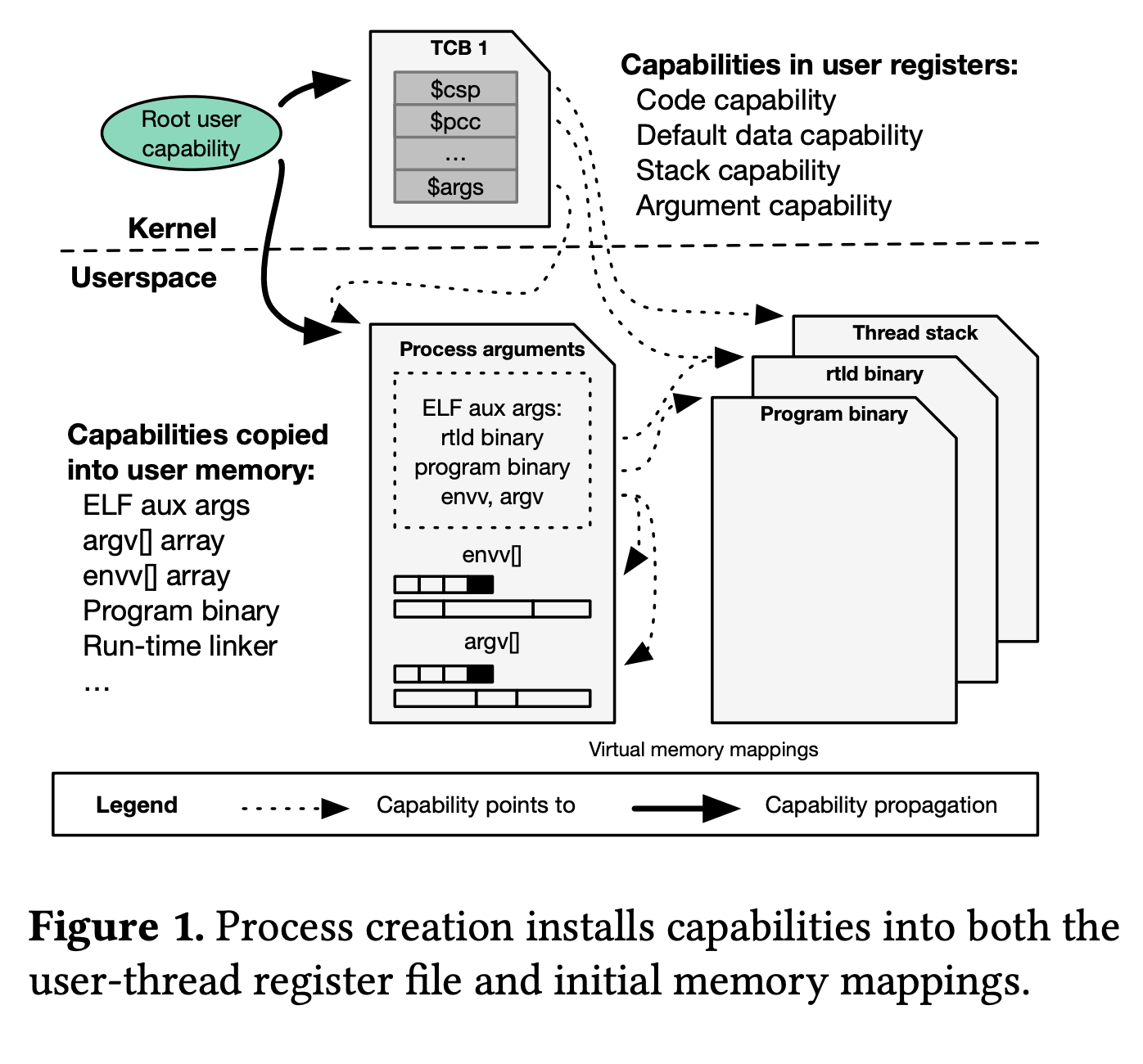
- CheriABI: Enforcing Valid Pointer Provenance and Minimizing Pointer Privilege in the POSIX C Run-time EnvironmentBrooks Davis , Robert N. M. Watson , Alexander Richardson , and 18 more authorsIn Proceedings of the Twenty-Fourth International Conference on Architectural Support for Programming Languages and Operating Systems , Providence, RI, USA, Apr 2019
Best paper award winner
The CHERI architecture allows pointers to be implemented as capabilities (rather than integer virtual addresses) in a manner that is compatible with, and strengthens, the semantics of the C language. In addition to the spatial protections offered by conventional fat pointers, CHERI capabilities offer strong integrity, enforced provenance validity, and access monotonicity. The stronger guarantees of these architectural capabilities must be reconciled with the real-world behavior of operating systems, run-time environments, and applications. When the process model, user-kernel interactions, dynamic linking, and memory management are all considered, we observe that simple derivation of architectural capabilities is insufficient to describe appropriate access to memory. We bridge this conceptual gap with a notional abstract capability that describes the accesses that should be allowed at a given point in execution, whether in the kernel or userspace. To investigate this notion at scale, we describe the first adaptation of a full C-language operating system (FreeBSD) with an enterprise database (PostgreSQL) for complete spatial and referential memory safety. We show that awareness of abstract capabilities, coupled with CHERI architectural capabilities, can provide more complete protection, strong compatibility, and acceptable performance overhead compared with the pre-CHERI baseline and software-only approaches. Our observations also have potentially significant implications for other mitigation techniques.
@inproceedings{2019cheriabi, author = {Davis, Brooks and Watson, Robert N. M. and Richardson, Alexander and Neumann, Peter G. and Moore, Simon W. and Baldwin, John and Chisnall, David and Clarke, James and Filardo, Nathaniel Wesley and Gudka, Khilan and Joannou, Alexandre and Laurie, Ben and Markettos, A. Theodore and Maste, J. Edward and Mazzinghi, Alfredo and Napierala, Edward Tomasz and Norton, Robert M. and Roe, Michael and Sewell, Peter and Son, Stacey and Woodruff, Jonathan}, title = {{CheriABI: Enforcing Valid Pointer Provenance and Minimizing Pointer Privilege in the POSIX C Run-time Environment}}, booktitle = {Proceedings of the Twenty-Fourth International Conference on Architectural Support for Programming Languages and Operating Systems}, isbn = {9781450362405}, publisher = {ACM}, address = {New York, NY, USA}, doi = {10.1145/3297858.3304042}, pages = {379-393}, numpages = {15}, location = {Providence, RI, USA}, series = {ASPLOS '19}, year = {2019}, month = apr, url = {https://www.microsoft.com/en-us/research/publication/cheriabi-enforcing-valid-pointer-provenance-and-minimizing-pointer-privilege-in-the-posix-c-run-time-environment/}, dimensions = {true}, }
2017
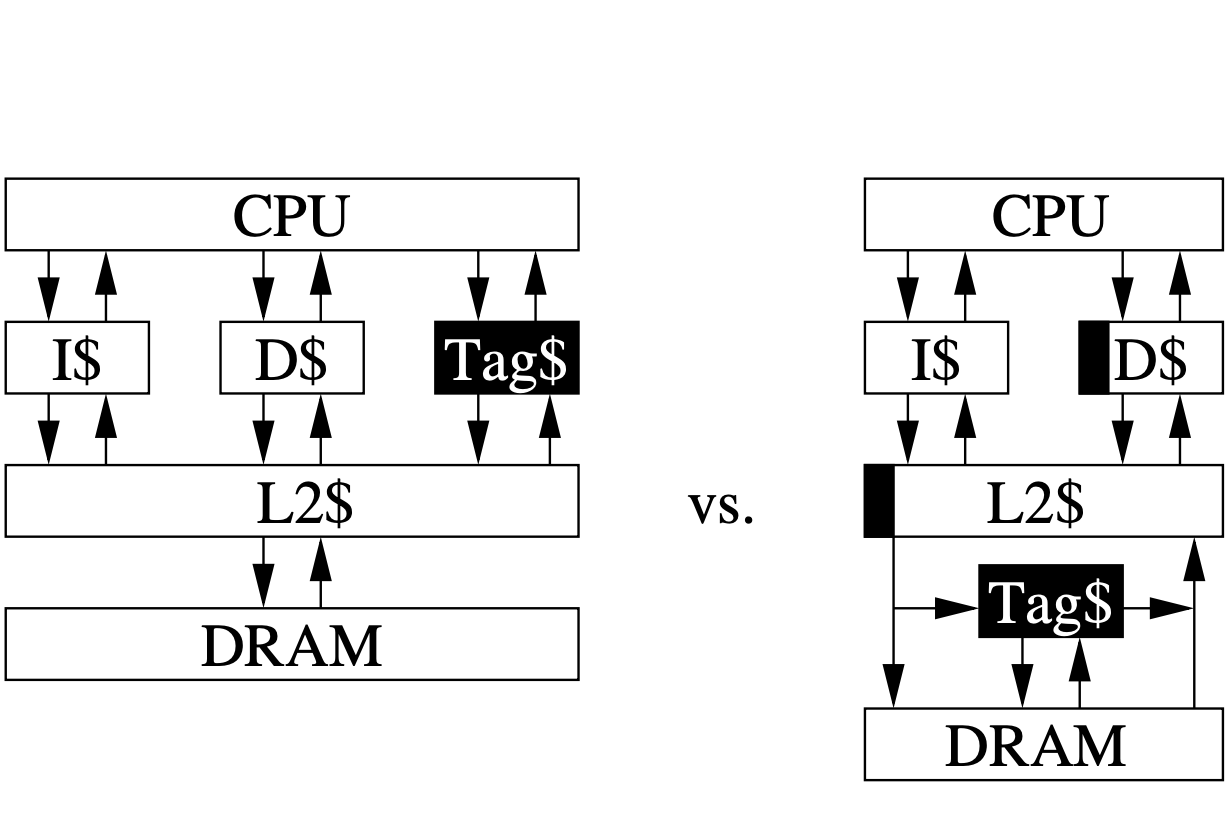
- Efficient Tagged MemoryAlexandre Joannou , Jonathan Woodruff , Robert Kovacsics , and 15 more authorsIn 2017 IEEE International Conference on Computer Design (ICCD) , Nov 2017
We characterize the cache behavior of an in-memory tag table and demonstrate that an optimized implementation can typically achieve a near-zero memory traffic overhead. Both industry and academia have repeatedly demonstrated tagged memory as a key mechanism to enable enforcement of powerful security invariants, including capabilities, pointer integrity, watchpoints, and information-flow tracking. A single-bit tag shadowspace is the most commonly proposed requirement, as one bit is the minimum metadata needed to distinguish between an untyped data word and any number of new hardware enforced types. We survey various tag shadowspace approaches and identify their common requirements and positive features of their implementations. To avoid non-standard memory widths, we identify the most practical implementation for tag storage to be an in-memory table managed next to the DRAM controller. We characterize the caching performance of such a tag table and demonstrate a DRAM traffic overhead below 5% for the vast majority of applications. We identify spatial locality on a page scale as the primary factor that enables surprisingly high table cache-ability. We then demonstrate tag-table compression for a set of common applications. A hierarchical structure with elegantly simple optimizations reduces DRAM traffic overhead to below 1% for most applications. These insights and optimizations pave the way for commercial applications making use of single-bit tags stored in commodity memory.
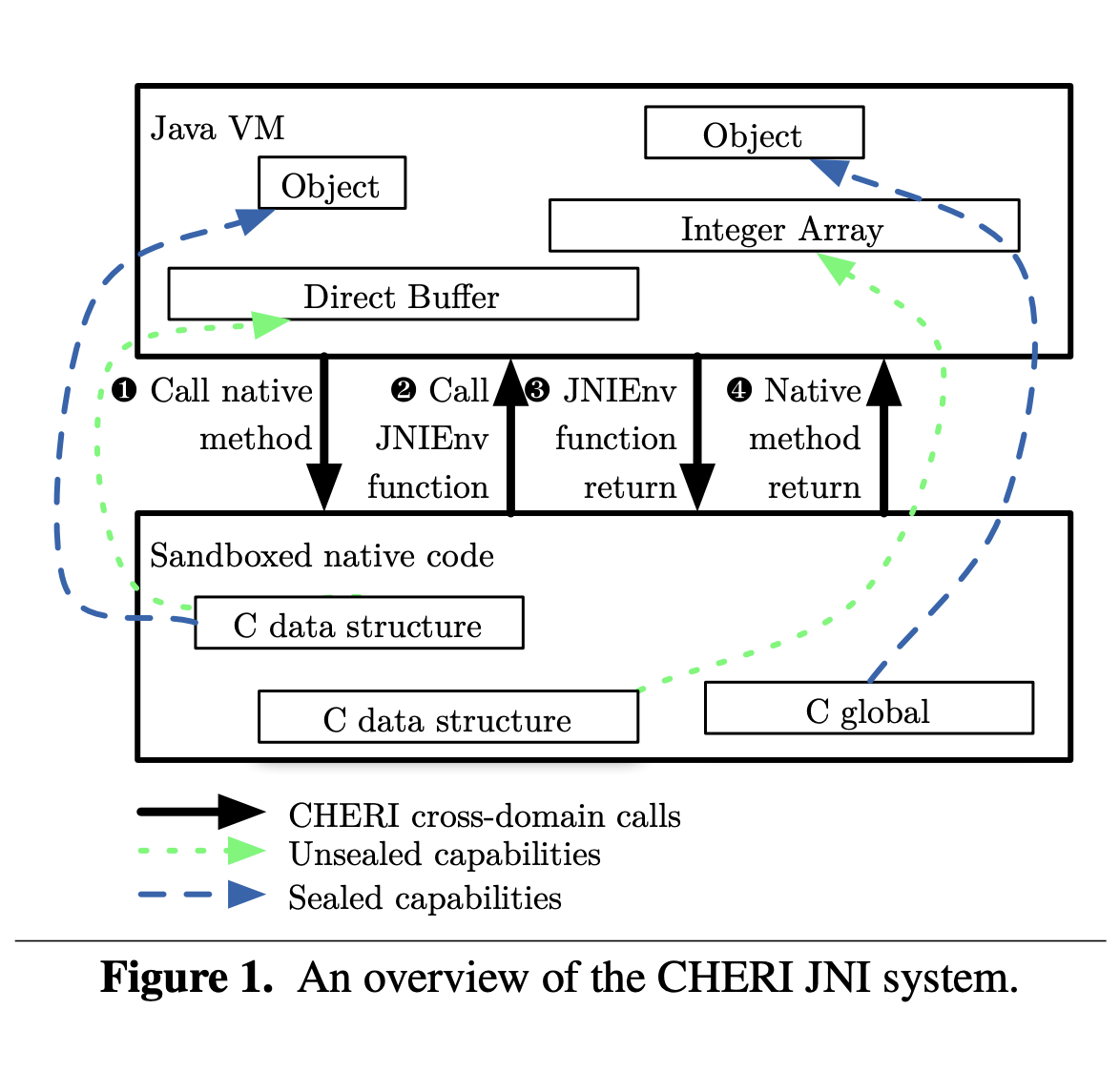
@inproceedings{2017efficienttags, author = {Joannou, Alexandre and Woodruff, Jonathan and Kovacsics, Robert and Moore, Simon. W. and Bradbury, Alex and Xia, Hongyan and Watson, Robert N. M. and Chisnall, David and Roe, Michael and Davis, Brooks and Napierala, Edward and Baldwin, John and Gudka, Khilan and Neumann, Peter G. and Mazzinghi, Alfredo and Richardson, Alex and Son, Stacey and Markettos, A. Theodore}, booktitle = {2017 IEEE International Conference on Computer Design (ICCD)}, title = {Efficient Tagged Memory}, year = {2017}, pages = {641-648}, keywords = {Computer architecture;Error correction codes;Hardware;Metadata;Pipelines;Random access memory;Security;Caches;Memory;Processor;Safety;Security}, doi = {10.1109/ICCD.2017.112}, issn = {1063-6404}, dimensions = {true}, month = nov } - CHERI JNI: Sinking the Java security model into the CDavid Chisnall , Brooks Davis , Khilan Gudka , and 11 more authorsIn Proceedings of the Twenty Second International Conference on Architectural Support for Programming Languages and Operating Systems , Xi’an, China, Nov 2017
Java provides security and robustness by building a high-level security model atop the foundation of memory protection. Unfortunately, any native code linked into a Java program – including the million lines used to implement the standard library – is able to bypass both the memory protection and the higher-level policies. We present a hardware-assisted implementation of the Java native code interface, which extends the guarantees required for Java’s security model to native code.
Our design supports safe direct access to buffers owned by the JVM, including hardware-enforced read-only access where appropriate. We also present Java language syntax to declaratively describe isolated compartments for native code.
We show that it is possible to preserve the memory safety and isolation requirements of the Java security model in C code, allowing native code to run in the same process as Java code with the same impact on security as running equivalent Java code. Our approach has a negligible impact on performance, compared with the existing unsafe native code interface. We demonstrate a prototype implementation running on the CHERI microprocessor synthesized in FPGA.@inproceedings{2017cherijni, author = {Chisnall, David and Davis, Brooks and Gudka, Khilan and Brazdil, David and Woodruff, Alexandre Joannouand Jonathan and Markettos, A. Theodore and Maste, J. Edward and Norton, Robert and Son, Stacey and Roe, Michael and Moore, Simon W. and Neumann, Peter G. and Laurie, Ben and Watson, Robert N. M.}, title = {{CHERI JNI}: Sinking the Java security model into the {C}}, booktitle = {Proceedings of the Twenty Second International Conference on Architectural Support for Programming Languages and Operating Systems}, series = {ASPLOS '17}, year = {2017}, location = {Xi'an, China}, publisher = {ACM}, address = {New York, NY, USA}, acmid = {3037725}, pages = {569--583}, numpages = {15}, isbn = {978-1-4503-4465-4}, keywords = {Java language, C language, bounds checking, capabilities, compilers, memory protection, memory safety, processor design, security}, dimensions = {true}, doi = {10.1145/3037697.3037725} }
2016
- Fast Protection-Domain Crossing in the CHERI Capability-System ArchitectureRobert N. M. Watson , Robert M. Norton , Jon Woodruff , and 16 more authorsIEEE Micro, Sep 2016
Capability Hardware Enhanced RISC Instructions (CHERI) supplement the conventional memory management unit (MMU) with instruction-set architecture (ISA) extensions that implement a capability system model in the address space. CHERI can also underpin a hardware-software object-capability model for scalable application compartmentalization that can mitigate broader classes of attack. This article describes ISA additions to CHERI that support fast protection-domain switching, not only in terms of low cycle count, but also efficient memory sharing with mutual distrust. The authors propose ISA support for sealed capabilities, hardware-assisted checking during protection-domain switching, a lightweight capability flow-control model, and fast register clearing, while retaining the flexibility of a software-defined protection-domain transition model. They validate this approach through a full-system experimental design, including ISA extensions, a field-programmable gate array prototype (implemented in Bluespec SystemVerilog), and a software stack including an OS (based on FreeBSD), compiler (based on LLVM), software compartmentalization model, and open-source applications.
@article{2016fast_domain_crossing, author = {Watson, Robert N. M. and Norton, Robert M. and Woodruff, Jon and Moore, Simon W. and Neumann, Peter G. and Anderson, Jon and Chisnall, David and Davis, Brooks and Laurie, Ben. and Roe, Michael and Dave, Nirav H. and Gudka, Khilan and Joannou, Alexandre and Markettos, A. Theodore and Maste, J. Edward and Murdoch, Steven J. and Rothwell, Colin and Son, Stacey D. and Vadera, Munraj}, url = {https://www.cl.cam.ac.uk/research/security/ctsrd/pdfs/20160728micro-journal-cheri-final.pdf}, journal = {IEEE Micro}, title = {Fast Protection-Domain Crossing in the CHERI Capability-System Architecture}, year = {2016}, volume = {36}, number = {5}, pages = {38-49}, keywords = {Capability engineering;Memory management;Program processors;Reduced instruction set computing;Systems modeling;CHERI;ISA;capabilities;capability;capability system;compartmentalization;hardware;instruction set architecture;memory management unit;memory protection;processor;security;software;vulnerability mitigation}, doi = {10.1109/MM.2016.84}, issn = {0272-1732}, dimensions = {true}, month = sep }
2015
- CHERI: A Hybrid Capability-System Architecture for Scalable Software CompartmentalizationRobert N.M. Watson , Jonathan Woodruff , Peter G. Neumann , and 12 more authorsIn 2015 IEEE Symposium on Security and Privacy , Sep 2015
CHERI extends a conventional RISC Instruction-Set Architecture, compiler, and operating system to support fine-grained, capability-based memory protection to mitigate memory-related vulnerabilities in C-language TCBs. We describe how CHERI capabilities can also underpin a hardware-software object-capability model for application compartmentalization that can mitigate broader classes of attack. Prototyped as an extension to the open-source 64-bit BERI RISC FPGA soft-core processor, Free BSD operating system, and LLVM compiler, we demonstrate multiple orders-of-magnitude improvement in scalability, simplified programmability, and resulting tangible security benefits as compared to compartmentalization based on pure Memory-Management Unit (MMU) designs. We evaluate incrementally deployable CHERI-based compartmentalization using several real-world UNIX libraries and applications.
@inproceedings{2015cheri, author = {Watson, Robert N.M. and Woodruff, Jonathan and Neumann, Peter G. and Moore, Simon W. and Anderson, Jonathan and Chisnall, David and Dave, Nirav and Davis, Brooks and Gudka, Khilan and Laurie, Ben and Murdoch, Steven J. and Norton, Robert and Roe, Michael and Son, Stacey and Vadera, Munraj}, booktitle = {2015 IEEE Symposium on Security and Privacy}, title = {CHERI: A Hybrid Capability-System Architecture for Scalable Software Compartmentalization}, year = {2015}, volume = {}, number = {}, pages = {20-37}, keywords = {Registers;Security;Kernel;Reduced instruction set computing;Libraries;Hardware;CHERI processor;capability system;software compartmentalization;computer architecture;memory protection;object capabilities}, doi = {10.1109/SP.2015.9}, dimensions = {true}, }